Difference between revisions of "Kaustubh Shivdikar"
m (JAXED PDF Added) (Tag: Visual edit) |
m (Moved content Index) (Tag: Visual edit) |
||
| Line 1: | Line 1: | ||
| − | + | == About Me == | |
| − | I am a Ph.D. candidate studying in [https://ece.northeastern.edu/groups/nucar/index.html NUCAR] lab at [https://www.northeastern.edu/ Northeastern University] under the guidance of [https://ece.northeastern.edu/fac-ece/kaeli.html Dr. David Kaeli]. My research focuses on designing '''hardware accelerators''' for '''sparse graph workloads'''. | + | I am a Ph.D. candidate studying in [https://ece.northeastern.edu/groups/nucar/index.html NUCAR] lab at [https://www.northeastern.edu/ Northeastern University] under the guidance of [https://ece.northeastern.edu/fac-ece/kaeli.html Dr. David Kaeli]. My research focuses on designing '''hardware accelerators''' for '''sparse graph workloads'''.[[File:Kaustubh Shivdikar Cropped and Mirrored Image.jpg|thumb|230x230px]]My expertise lies in: |
| − | |||
| − | My expertise lies in: | ||
*Computer Architecture Simulator Design | *Computer Architecture Simulator Design | ||
Revision as of 19:24, 19 August 2022
Contents
About Me
I am a Ph.D. candidate studying in NUCAR lab at Northeastern University under the guidance of Dr. David Kaeli. My research focuses on designing hardware accelerators for sparse graph workloads.
My expertise lies in:
- Computer Architecture Simulator Design
- Graph Neural Network Accelerators
- Sparse Matrix Accelerators
- Homomorphic Encryption Accelerators
- GPU Kernel Design
Contact: shivdikar.k [at] northeastern [dot] edu, mail [at] kaustubh [dot] us
Education
- Ph.D., Compuer Engineering, Northeastern University, Boston [Expected Fall 2022]
- M.S., Electrical and Computer Engineering, Northeastern University, Boston [May 2021]
- B.S., Electrical Engineering, Veermata Jijabai Technological Institute, University of Mumbai, India [May 2016]
Work
- Summer-Fall 2020 Coop: Parallel Computing Lab (Fabrizio Petrini), Intel, developed novel architectural features.
- Summer-Fall 2019 Coop: Parallel Computing Lab (Fabrizio Petrini), Intel, designed SpGEMM kernels for Intel’s new architecture.
- Summer-Fall 2018 Coop: Omron Adept (George Paul), implemented parallel graph traversal algorithms for Robot Path Planning.
Recent News
- May 2022: Served Submission co-chair for HPCA 2022 conference.
- April 2019: Graduate Innovator Award at the RISE 2019 Research Expo for our poster Pi-Tiles
- April 2018: Best Poster Award at the RISE 2018 Research Expo for our poster The Prime Hexagon
- November 2018: Mentored the NEU team for Student Cluster Contest at Super Computing Conference 2018
- November 2017: Joined the NEU Team for Student Cluster Contest at Super Computing Conference 2017
Publications
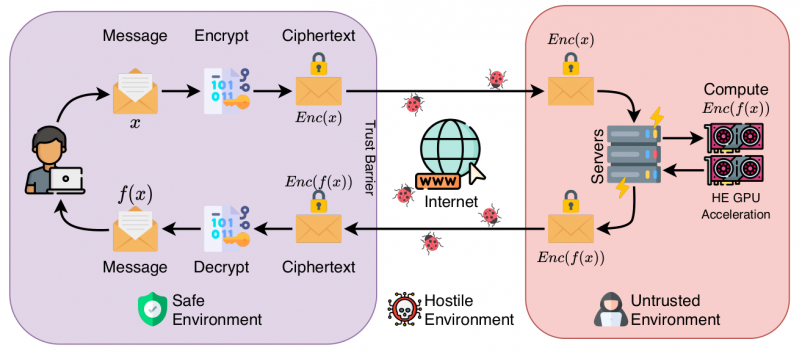
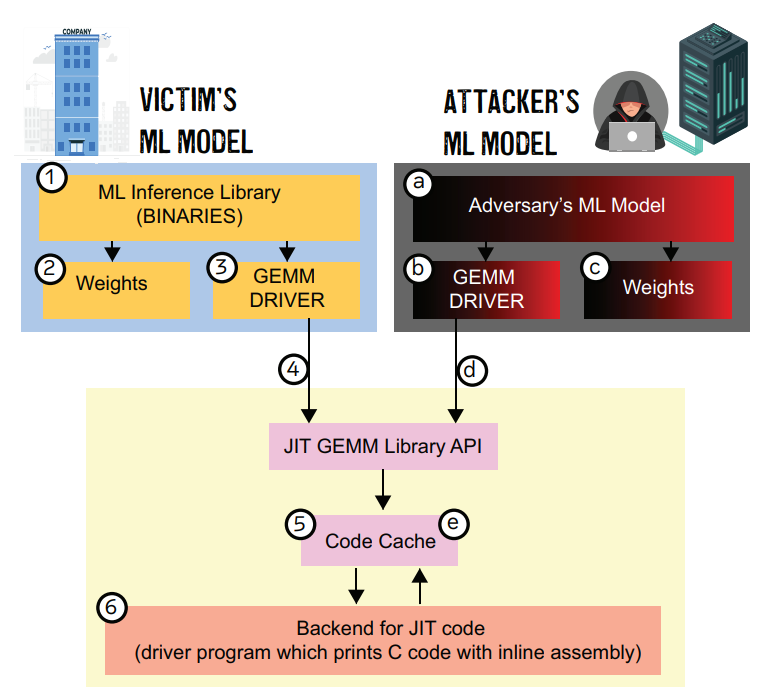
- Accelerating Polynomial Multiplication for Homomorphic Encryption on GPUs (SEED 2022) [PDF]
- GNNMark: A benchmark suite to characterize graph neural network training on GPUs (ISPASS 2021)
- SMASH: Sparse Matrix Atomic Scratchpad Hashing (MS Thesis, 2021)
- Student cluster competition 2018, team northeastern university: Reproducing performance of a multi-physics simulations of the Tsunamigenic 2004 Sumatra Megathrust earthquake on the AMD EPYC 7551 architecture (SC 2018)
- Speeding up DNNs using HPL based Fine-grained Tiling for Distributed Multi-GPU Training (BARC 2018)
- Video steganography using encrypted payload for satellite communication (Aerospace Conference 2017)
- Missing'Middle Scenarios' Uncovering Nuanced Conditions in Latin America's Housing Crisis (Cityscape 2017)
- Dynamic power allocation using Stackelberg game in a wireless sensor network (Aerospace Conference 2016)
- Automatic image annotation using a hybrid engine (Indicon 2015)
What is KTB Wiki?
This website was built on KTB Wiki. KTB wiki is my side project/attempt to consolidate knowledge gained during my Ph.D. journey. Though many other platforms provide similar service, the process of creating KTB Wiki was a learning experience since it taught me concepts indexing, load balancing, and in-memory file systems. KTB Wiki was built using MediaWiki and is intended for research purposes only.
KTB Wiki, because the best way to store your knowledge is in an indexed SQL database.
Hobbies
Interesting Reads
Coming soon...